This is urgent and you should act immediately. If you are running Windows and Windows Server machines you should disable the Print Spooler service and disallow client connection. This also applies to domain controllers as they are also affected.
But, why? A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. In other words, an attacker could have full access to your Windows environment.
Jul 1, 2021: Microsoft is aware of and investigating a remote code execution vulnerability that affects Windows Print Spooler and has assigned CVE-2021-34527 to this vulnerability. Microsoft is working on an update to protect from this vulnerability.
Jul 7, 2021: Microsoft has released patches for several versions of Windows to address the CVE-2021-34527 vulnerability. You can download it on this LINK.
https://msrc.microsoft.com/
RECOMMENDATION
Run Windows Update – In the first place, you should apply the security updates released on June 8, 2021. You can run it through Windows Update or WSUS.
Disable Print Spooler – Open Services applet from Control Panel or by typing services into Start Menu and navigate to the Print Spooler > General > Disable > and then Stop it!

Disallow incoming connections – in order to block remote attacks, you should disable incoming connections to Print Spooler by creating a group policy on domain level and applying it to your computers via Computer Configuration > Administrative Templates > Printers > Allow Print Spooler to accept client connections > Disabled
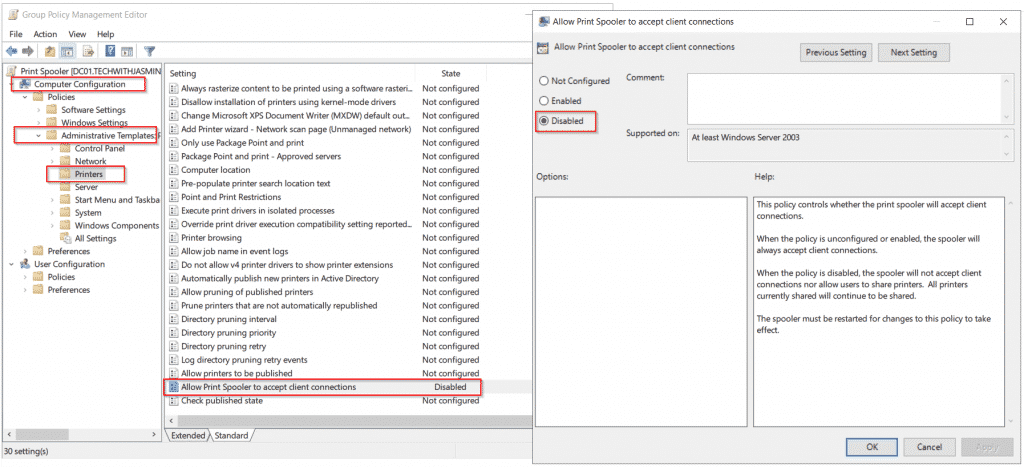
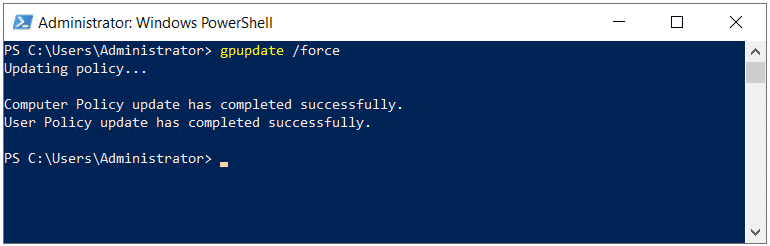
Once you are done, open PowerShell or CMD and type gpupdate /force to apply group policy change immediately. By default, it applies after 90 minutes or after user sign out/ sign in.
According to Microsoft: “To reduce the attack surface and as an alternative to disabling printing, check membership and nested group membership in the groups listed below. Attempt to reduce membership as much as possible, or completely empty the groups where possible. Due to legacy configurations and backwards compatibility, some of these groups may contain Authenticated Users or Domain Users, which would allow anyone in the domain to exploit the domain controller.”
- Administrators
- Domain Controllers
- Read Only Domain Controllers
- Enterprise Read Only Domain Controllers
- Certificate Admins
- Schema Admins
- Enterprise Admins
- Group Policy Admins
- Power Users
- System Operators
- Print Operators
- Backup Operators
- RAS Servers
- Pre-Windows 2000 Compatible Access
- Network Configuration Operators Group Object
- Cryptographic Operators Group Object
- Local account and member of Administrators group
Note: Removing members from these groups may cause other compatibility problems.
Please share this article with other IT folks by clicking on social media button below.